Network and cloud security protect every digital process running across connected systems. Each layer, from the physical cables on a server rack to the user applications in the cloud, plays a role in defending data, preventing breaches, and maintaining trust in modern organizations. Understanding how these seven layers work helps you build a complete defense strategy instead of relying on isolated tools. This article explains the seven layers, the threats they face, and how students preparing for cybersecurity careers can apply this framework in real workplaces.
Key Takeaways:
- Network and cloud security rely on seven interconnected layers that defend data from end to end.
- Knowing the vulnerabilities within each OSI layer prepares students to prevent common cyberattacks.
- Learning cloud-ready security practices improves employability in IT, data analytics, and infrastructure roles.
What are Network and Cloud Security and How Do They Work?
Network and cloud security refer to the combined practices that protect data, applications, and systems from unauthorized access or disruption. In traditional networks, security measures safeguard devices and on-premises servers. In cloud environments, protection extends to virtual infrastructure, cloud storage, and distributed services managed by external providers. Both environments share one purpose: defending information integrity through structured, layered control.
Each layer has its own threats and protection methods. A firewall at the perimeter might block suspicious traffic, while encryption safeguards data traveling between users and cloud servers. Identity management systems confirm user authenticity, ensuring that only approved individuals access company resources. Together, these mechanisms create depth, security that does not fail if a single defense point is compromised.
For students entering IT or cybersecurity careers, understanding these layers is critical. Employers expect professionals who can design systems that remain safe under pressure. Courses such as SQL Programming and Machine Learning and Big Data Analytics at Metro College help you interpret security data, automate detection, and apply technical precision in cloud environments.
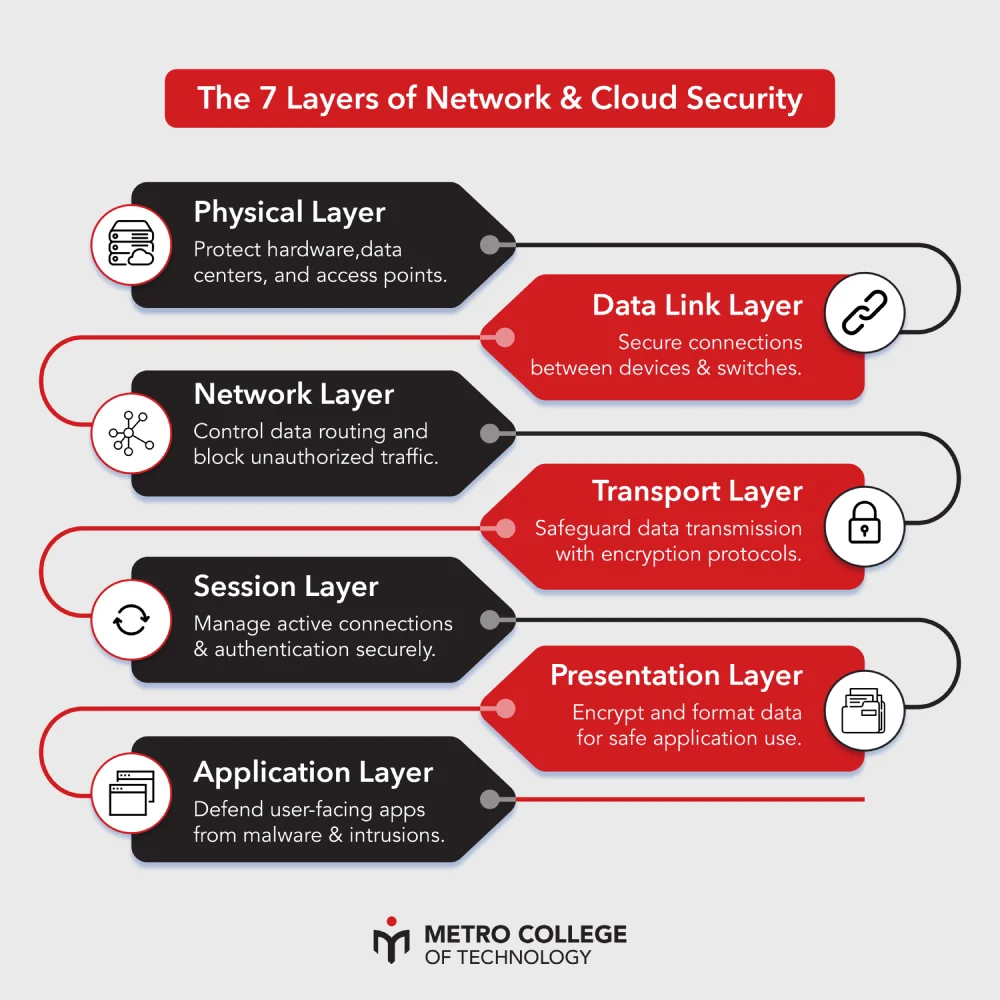
7 Layers of Network and Cloud Security That You Should Know About
Understanding the seven layers of security aligns directly with the OSI (Open Systems Interconnection) model. Each layer represents a unique set of responsibilities and vulnerabilities. When combined, they provide a blueprint for securing both local networks and multi-cloud architectures. Students learning cybersecurity must grasp how data flows through these layers to identify where risks emerge and how to control them effectively.
In today’s hybrid IT environment, threats can appear anywhere along the path, from hardware failures to malicious code. Applying layered defense means distributing controls across every stage, making it difficult for attackers to move laterally once they enter the system. This section explores each layer in detail and connects their functions to practical applications in network and cloud security.
A professional who understands these seven layers not only prevents system failures but also enhances system performance. The same principles used to safeguard servers can optimize traffic flow, minimize latency, and support compliance with data protection regulations. These competencies translate into high-demand roles in network administration, cloud architecture, and cybersecurity analysis.
1. Physical Layer
The physical layer is where hardware and physical connections exist, servers, cables, routers, and wireless access points. Security here focuses on controlling physical access to these components. Unauthorized entry into data centers or tampering with cabling can lead to outages or information theft.
Protection includes locked server rooms, surveillance systems, and environmental monitoring. Students learning network and cloud security must understand how physical safeguards complement digital defenses. Even the most sophisticated encryption cannot prevent a security breach if someone gains direct access to the equipment.
2. Data Link Layer
The data link layer manages communication between network nodes within the same local area network (LAN). It ensures data frames are transmitted correctly between devices. Security at this level involves controlling traffic to prevent spoofing, MAC address manipulation, and man-in-the-middle attacks.
Techniques like VLAN segmentation and MAC filtering reduce unauthorized communication. Learning how switches and bridges maintain data integrity teaches students to secure local networks that connect to broader cloud systems. This foundation supports more advanced security designs later in their careers.
3. Network Layer
The network layer is responsible for routing data between systems through IP addresses. Attackers often exploit this layer to perform IP spoofing, denial-of-service (DoS), or routing table manipulation. Strong configuration and monitoring practices help stop these threats.
Firewalls, intrusion detection systems, and access control lists (ACLs) form the primary defenses at this level. Students learning analytics through Data Science (SAS + Python) develop the ability to interpret traffic logs, detect anomalies, and build secure network policies. Mastering these processes improves employability in roles that require both analytical and operational expertise.
4. Transport Layer
The transport layer ensures reliable communication between networked devices. Protocols such as TCP and UDP manage how data packets are sent and received. Attackers may target this layer through session hijacking, port scanning, or packet injection.
Security strategies include encryption (like TLS) and port management to limit exposure. By learning how encryption protocols operate, students gain the ability to secure online transactions and cloud data exchanges. Understanding the transport layer also prepares professionals to maintain availability under high traffic loads, a critical skill in e-commerce and financial systems.
5. Session Layer
The session layer manages ongoing communication between devices, maintaining open sessions while data is exchanged. Insecure session handling can allow attackers to steal credentials or impersonate users. Authentication tokens and session timeouts help protect this layer.
Professionals working in cybersecurity often configure authentication servers and session management systems to prevent unauthorized persistence. Automation and anomaly detection often rely on skills supported by programs like Python for Data Analytics.
6. Presentation Layer
The presentation layer formats and encrypts data so it can be properly understood by applications and users. This layer converts information into readable forms while keeping sensitive details hidden through encryption and compression.
Misconfigurations here can expose private data or create compatibility problems across systems. Analytics training like Digital Media Marketing & Analytics helps future professionals understand data transformation and visualization securely. Students who understand this layer can design systems that balance readability with security precision.
7. Application Layer
The application layer sits closest to the end user. It governs protocols such as HTTP, SMTP, and FTP. Most modern cyberattacks, including phishing, malware injection, and API exploitation, target this layer directly.
Application firewalls, secure coding practices, and continuous monitoring guard against these attacks. Professionals who combine technical programming knowledge with data analytics can detect behavioral anomalies before they escalate. By understanding this final layer, students learn to secure the entire communication chain from user interface to database storage.

Build a Future in Cloud Network Security
Gain hands-on experience securing cloud systems, analyzing security logs, and applying encryption techniques used across enterprise IT infrastructures.
Common Cyber Attacks Targeting Each OSI Layer and How to Defend Against Them
Every OSI layer presents an opportunity for exploitation. Understanding how these attacks operate helps students design defense strategies for each stage of communication. A single weak point can compromise entire systems, which is why layered protection remains the foundation of effective network and cloud security.
Frequent attack types and defenses include:
- Physical Attacks: Hardware theft or tampering. Secure access with biometric locks and 24-hour surveillance.
- Data Link Exploits: MAC flooding or ARP spoofing. Use VLAN segmentation and port security on switches.
- Network-Level Intrusions: DoS attacks or routing corruption. Deploy firewalls, IDS systems, and rate-limiting controls.
- Transport Layer Attacks: Session hijacking or SYN flooding. Configure TLS encryption and limit open ports.
- Session Compromise: Token theft or replay attacks. Implement session expiration and multi-factor authentication.
- Presentation Layer Breaches: Data manipulation or encryption bypass. Standardize data formatting and verify encryption algorithms.
- Application Exploits: Malware injection or phishing. Conduct code audits, train employees, and deploy application firewalls.
Learning these methods during your studies prepares you to act as a first responder when incidents occur. The ability to recognize early warning signs sets strong candidates apart during cybersecurity interviews.
Best Practices for Securing Hybrid and Multi-Cloud Infrastructures
Modern companies often operate across multiple cloud providers. Hybrid and multi-cloud infrastructures combine on-premises systems with public or private cloud platforms, increasing flexibility but also expanding the attack surface. Managing this complexity requires structure, awareness, and consistent policy enforcement.
Strong multi-cloud security depends on visibility, governance, and automation. A single oversight in configuration can expose sensitive information. Students mastering network and cloud security should learn how orchestration tools, analytics, and automation scripts integrate to maintain compliance across environments.
Best practices include:
- Centralized Identity Management: Use unified authentication systems across all environments to control access consistently.
- Encryption Everywhere: Apply encryption to both data in transit and at rest, ensuring confidentiality across connected platforms.
- Automated Compliance Checks: Deploy automation scripts built using Python or SQL queries to detect misconfigurations in real time.
- Zero-Trust Policies: Verify every device and user before granting access, regardless of network location.
- Continuous Monitoring: Use analytics dashboards powered by Tableau or similar tools to track performance and detect anomalies.
Following these methods helps future professionals maintain stable, secure cloud ecosystems, a skill set increasingly demanded by employers across finance, healthcare, and manufacturing sectors.
The Importance of Network Segmentation and Micro-Segmentation in Layered Security
Segmentation divides a network into smaller, manageable parts to restrict traffic between systems. It isolates sensitive resources, limiting the spread of malware or unauthorized access. Without segmentation, a single compromised device could jeopardize an entire network.
Network segmentation uses VLANs, subnets, and firewalls to enforce separation between departments or workloads. Micro-segmentation extends these principles deeper into virtualized and cloud environments, where traditional perimeters no longer exist. Policies define which virtual machines or containers can communicate, creating an additional layer of defense.
For students studying cybersecurity architecture, understanding segmentation aligns with both strategy and compliance. Machine learning programs such as Data Science (SAS + Python) prepares students to analyze traffic patterns and support segmentation strategies. Graduates with these competencies can design resilient infrastructures that meet regulatory standards and minimize downtime after incidents.
Segmentation also contributes to operational efficiency. When traffic is organized, troubleshooting becomes faster, system performance improves, and resource allocation is easier to manage. Building this knowledge positions you to design future networks where speed and safety coexist naturally.
FAQ
What careers can you pursue with network and cloud security skills?
Graduates can work as cybersecurity analysts, network administrators, or cloud security engineers. Employers seek individuals who understand system architecture, risk management, and compliance. Knowledge of the seven OSI layers proves invaluable when designing and maintaining secure infrastructures.
Why are certifications and technical courses valuable for cybersecurity students?
Certifications verify that you can apply knowledge in real scenarios. Short programs in SAS, Python, and SQL enhance employability by combining technical skill with analytical thinking. Employers often prioritize certified candidates who can immediately contribute to ongoing projects.
How can data analytics support network and cloud security?
Analytics identifies trends and detects anomalies before they escalate. Integrating data analysis tools such as Tableau allows professionals to visualize traffic, identify vulnerabilities, and improve decision-making. These skills turn raw information into actionable intelligence that strengthens every layer of defense.
Monitoring and Incident Response Strategies Aligned with OSI Layer Security
Network and cloud security succeed when monitoring and response align with every OSI layer. A comprehensive plan means knowing how to detect abnormal behavior at the physical, network, and application levels simultaneously. Data analytics, automation, and structured playbooks give teams clarity during a crisis.
For students building cybersecurity careers, mastery of layered monitoring transforms theory into action. Each alert, log, and metric contributes to faster incident containment and reduced downtime. By learning these principles now, you prepare to design resilient systems that adapt to evolving digital threats and keep operations stable for the businesses you will serve.
Network and cloud security continue to define the backbone of digital transformation. The more you understand these seven layers, the stronger your role becomes in protecting the data, trust, and performance that drive modern organizations forward.

Prepare for a Career Securing Cloud Networks
Learn cloud defense techniques, automation workflows, and real-world security tools through Metro College’s industry-focused training programs.